Two weeks have passed since last post, what happened since then?
Pinentry Prompts
Pinentry is an application to handle prompts for GnuPG, it should be able to ask for passwords and make questions.
Passwords of gpg keys can be stored in gnome-keyring through pinentry-gnome3.
As I talked in last post, some prompt types are not handled by gcr, these types are confirm prompts with one button, and confirm prompts with three buttons.
One button prompts are to inform/notify of something. They have only one way out, clicking the button, which means the message has been read and understood by the user. If the prompt is not system modal it still can be closed through right upper corner X button, but the outcome is the same as if the user clicked the button.

One-button prompt – Your passphrase is insecure
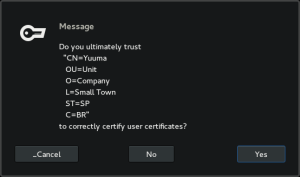
Three button prompts are to ask user a question and provide three answer options, the answers are, by default, “Cancel”, “Not ok”, and “Ok”. They are useful in situations when answering “Not ok” should trigger something that “Cancel” doesn’t, sounds obviuos. An example, can help explain:
The prompt above is shown when adding a new root S/MIME certificate. If you cancel the operation, the certificate won’t be added, and that’s it. Clicking in No, will add the certificate to the trust list as not trusted, and future attempts to add the certificate will be denied automatically. Whereas clicking in Yes will proceed to the following prompt.
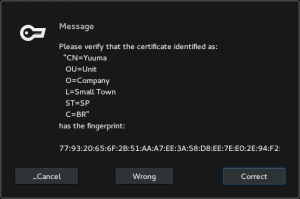
Here, this prompt has the same behavior for the three buttons.
Not supporting these prompts doesn’t mean that pinentry-gnome3 will not work, but user experience might not be the expected.
GnuPG supports pinentry programs without one-button and three-button prompts. In situations where there would be only one button, there will be two buttons, and one of them providing weird functionality.
Let me explain what I mean, in the sample one-button prompt above the user is generation a new gpg-key, passphrase constraints are enforced and the user has entered a short passphrase, so GnuPG has issued that prompt. The user must choose another passphrase!
Wether the user chooses to cancel, or enter the new passphrase, the return of the prompt is ignored and is unconditionally taken again to the password prompt to enter a new passphrase. The cancel button won’t work as expected and the user has to click cancel again in the prompt password to cancel the operation.
In the three-button prompt use case presented above, the certificate won’t be added to trust list as not trusted if the user does not trust the certificate or finds out that certificate fingerprint is wrong.
I started implementing these button prompts in Gcr and GNOME Shell right away, but I realized that to be a mistake without first discussion.
Stef is concerned with usability issues that may come up with a non-cancelable one button prompt. These one-button prompts could also be presented as gnome-shell notifications, but as cited before, in the presented use case a system modal prompt is issued again, and the notification may go unnoticed. Also, checking the fingerprint of certificates can be very difficult with system modal prompts, since it locks the entire screen.
GNOME Shell Prompt and mnemonics
You can see through above prompts that some buttons have a leading underscore, those are mnemonics for buttons set by GnuPG. Currently, gnome-shell system modal prompts don’t support mnemonics. So a fix has been made to strip out mnemonics indicators. An other usability issue here a feature existent in many pinentry programs is not available in pinentry-gnome3.
pinentry-gnome3 and gnome-keyring together
A new version of Pinentry which includes pinentry-gnome3 was released and Stef removed gpg-agent component from gnome-keyring.
We were looking for ways to tie pinentry-gnome3 and gnome-keyring together.
Our concern is to ensure that when gnome-keyring is running along with gpg in a GNOME session it can cache gpg passphrases if opted to. It may be easier to thinking the other (practical) way, how to ensure that gpg launches pinentry-gnome3 when running a GNOME session.
The suggested work is to make gnome-keyring depend on pinentry-gnome3 and tie gpg to pinetry-gnome3 through update-alternatives, gpgconf or pinetry-wrapper. I might discuss more about this in future posts.
Currently working
Current efforts are directed to resolving a possible bug between gpg and pinetry-gnome3 related to DBUS.